The US National Institutes of Standards and Technology recently asked for comments on a new framework for secure software development. Called Mitigating the Risk of Software Vulnerabilities by Adopting a Secure Software Development Framework (SSDF), this framework seeks to aid developers by providing a somewhat universal framework for secure software development. However, what this framework doesn't do is provide explicit rules. Instead, as the name clarifies, it is a framework or guide.
The Framework is a short 19 pages, many of which are definitions, references, etc. That's good because that makes the document readable and understandable, and users will not get bogged down in many guidelines.
Audience
Unlike some other NIST documents, this one is designed for a broad audience:
There are two primary audiences for this white paper. The first is software producers (e.g., commercial-off-the-shelf [COTS] product vendors, government-off-the-shelf [GOTS] software developers, custom software developers) regardless of size, sector, or level of maturity. The second is software consumers, both federal government agencies and other organizations. Readers of this document are not expected to be experts in secure software development to understand it, but such expertise is required to implement its recommended practices.
Structure Of The Framework
The Framework is divided into four groups:
Prepare the Organization (PO)
Ensure the organization's people, processes, and technology are prepared for secure software development.
Protect the Software (PS)
Protect all software components from tampering and unauthorized access.
Produce Well-Secured Software (PW)
Produce well-secured software with minimal security vulnerabilities in its releases.
Respond to Vulnerability Reports (RV)
Identify vulnerabilities in software releases and respond appropriately to address those vulnerabilities and prevent similar vulnerabilities from occurring.
NIST Whitepaper
The actual items in the whitepaper look like this:
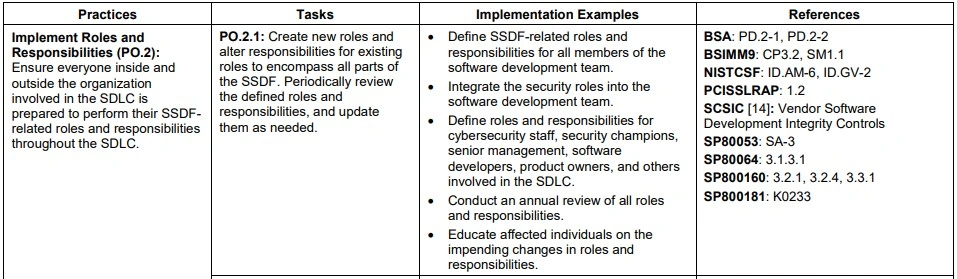
There are two Tasks Associated with this particular Practice so that you can refer to them individually in a document or discussion. The wording is straightforward and not tangled in legalese. The copious list of referenced documents is listed in the Framework so readers can get a more detailed description of the Task. In addition, the suggestions in the Implementation Examples column show how an organization might implement a particular Task.
Benefits Of A Framework
A workable framework will provide civilian and government organizations with a starting point for developing secure software. After reading the document, it will be clear that this is not a "how-to" for individual programmers but rather a guide for creating the proper environment for secure development.
This Framework document continues their effort to make the software more secure (and there are other steps they have outlined). I applaud this effort. Preventing software vulnerabilities is hard. Individual pieces of software, such as an operating system, language compiler, or a comprehensive web server, are pretty complex. The news is full of reports of breaches and other software failures. The more we can do, the better.
The comment period for this document expired on August 8th, 2019, and you may be reading this after that. That's alright: the point is that the effort is ongoing and will hopefully lead to more secure software.
To your safe computing!
This piece was originally posted on October 15, 2019, and has been refreshed with updated styling.


